Best practices to prevent phishing attacks, part 2
In the first part of this article we explained what is phishing and how to identify email scams. In this article we’ll talk about the scam websites and how they try to deceive us by impersonating another site.
![Best practices to prevent phishing attacks, part 2 [2017]](https://www.briskbard.com/blog/images/phishing_400.jpg)
The purpose of these fraudulent websites is the same as the email messages with phishing. They try to deceive users by appearing to be a trusted website to steal personal information or to install malware. That malware can be used to infect computers with viruses or to wreak havoc in a corporate network.
To recognize fraudulent websites you have to take a look at the following characteristics :
Internet address
The website’s Internet address must belong to the domain of the company shown in the contents of that page. For example, if the web page looks like a page from a certain bank, its Internet address must belong to the bank’s domain.

To identify suspicious domains you have to use the same criteria about Internet addresses explained in the first part of this article.
To increase your safety, it’s recommended to make sure you use the right Internet address by searching the name of the company in a web search engine or in local business directories. Many businesses from the US, Canada and Mexico can be found at the Better Business Bureau.
Another way to check who’s the owner of a given Internet address is by searching it with WhoIs. WhoIs gives you information regarding a domain name and it can be obtained by using the developer tools in BriskBard or by visiting the ICANN website.
If the WhoIs information doesn’t match with the name of the company shown in the contents of that page, you shouldn’t trust that website.
Secure connection
Many of the services available in Internet need to establish a secure connection with each user, for example banks, shops, government sites, etc.

We must reject any web page that supposedly offers one of those services using an insecure connection in the web browser.
To identify the secure connections you can check these features :
-
The Internet address start with HTTPS in secure connections. If it starts with HTTP (without an S) the connection is insecure.
-
The web browser shows a lock next to the web page’s address.
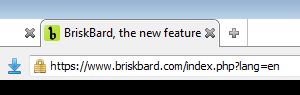
Some web browsers allow the user to see the information of the security certificate used in that web page when they click on the lock icon. That certificate must be valid and it must belong to the company shown in the web page’s content.
Contents
The creators of fraudulent web pages usually make incomplete copies of the original website. If you can’t find all the web pages or some of the important pages like the legal notes or the contact information is missing, you should be wary of that website.

On some occasions the fraudsters include grammar or spelling mistakes. All big corporations check the text in their public documents several times and even if a mistake is not detected, it wouldn’t last for long.
The fraudulent web pages use the same tricks and persuasion techniques used in the phishing email messages explained in the first part of this article :
-
Products too good to be true.
-
Urgency.
-
Herd behavior.
-
Authority.
-
Reciprocity.
-
Exclusivity.
-
Appeal to feelings.
-
Curiosity.
-
Etc.

These scam websites may even ask you to use an insecure payment method like bank transfers.
Checking for phishing and malware
Web browsers usually check all visited web pages automatically using on-line databases which contain hundreds of thousands of scam websites.
While other web browsers only use one phishing database, BriskBard can use 3 for greater user safety.
BriskBard can use PhishTank and Google SafeBrowsing for automatic checks, and for manual checks it can use Google SafeBrowsing and Yandex SafeBrowsing.
You can also check manually if a web page is a scam or it’s a malware distribution site by using these services :
https://www.google.com/transparencyreport/safebrowsing/diagnostic/
http://www.avgthreatlabs.com/ww-en/website-safety-reports/
In case you downloaded a file from a suspicious website you can scan it with these services :
Fraud examples
Among the most common cases of scams there are many that try to impersonate these websites :
-
Tax agencies.
-
Banks.
-
Shops.
-
Internet payment gateways.
-
Credit card companies.
-
Auction sites.
-
Social networks.
-
Lotteries.
-
Job search sites.
-
Antivirus creators.
Conclusion
As a final recommendation, don’t forget to keep updated your operating system, your antivirus and your web browser.
Don’t disable any anti-phishing protection in the web browser and consider using an alternative DNS server that blocks malicious sites.
Don’t trust blindly in any web page that asks for private data and don’t visit websites offering pirated or illegal products. Ignore all warnings from some of those pages about supposed virus infections in your computer.
Remember that you shouldn’t click on any link found in email messages or Usenet newsgroups articles.
Disclosure Statement: This site and BriskBard contains affiliate links, which means that I may receive a commision if you make a purchase using these links. As an eBay Partner, I earn from qualifying purchases.